NCP Secure Entry
NCP Secure Entry
NCP Secure Entry is a secure remote access solution that allows users to securely connect to corporate resources from any device or location. It provides endpoint security, multi-factor authentication, and granular access controls.
What is NCP Secure Entry?
NCP Secure Entry is a secure remote access solution designed to provide simple yet highly secure connectivity for remote users and branch offices. It enables companies to give users access to sensitive corporate resources while ensuring endpoint security, access control, and compliance.
Key features of NCP Secure Entry include:
- Secure encrypted connectivity using SSL VPN and IPsec VPN protocols
- Multi-factor authentication including one-time passwords, tokens, and smart cards
- Host Checker for pre- and post-connect endpoint security assessments and enforcement
- Centralized granular access and authorization controls based on users, groups, time, location etc.
- Application Layer VPN for securing access to specific apps and resources
- Optimized connectivity modes for desktops, laptops, smartphones and tablets
- Centralized management console for configuring secure access policies
- Comprehensive logging, reporting and auditing capabilities
- Scalable architecture that supports up to 100,000 concurrent VPN connections
With its focus on secure endpoint access and granular policy enforcement, NCP Secure Entry serves as a complete endpoint security and remote access solution for today's mobile and distributed enterprises.
NCP Secure Entry Features
Features
- Secure remote access
- Multi-factor authentication
- Endpoint security
- Granular access controls
- VPN access
- Single sign-on
Pricing
- Subscription-Based
Pros
Cons
Reviews & Ratings
Login to ReviewThe Best NCP Secure Entry Alternatives
Top Security & Privacy and Remote Access and other similar apps like NCP Secure Entry
Here are some alternatives to NCP Secure Entry:
Suggest an alternative ❐Psiphon
Proton VPN
Hoxx VPN Proxy
CyberGhost VPN
Hotspot Shield
Windscribe
FreePN
ZenMate
VPN Unlimited
Yggdrasil
UTunnel VPN

Bitmask

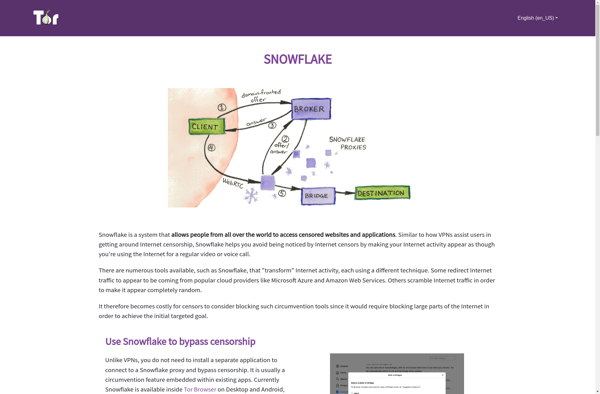
Snowflake Tor